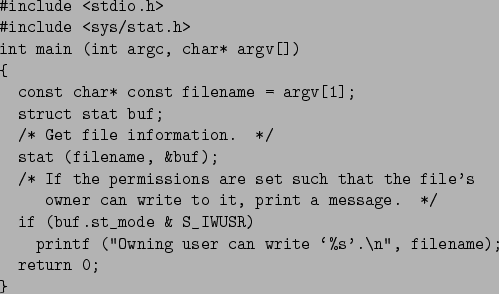
$ ./stat-perm hello
chmod ("hello", S_IRUSR | S_IXUSR);
- If a user is allowed to read from a directory, the user is allowed to see the list of files that are present in that directory.
- If a user is allowed to write to a directory, the user is allowed to add or remove files from the directory. Note that a user may remove files from a directory if she is allowed to write to the directory, even if she does not have permission to modify the file she is removing.
- If a user is allowed to execute a directory, the user is allowed to enter that directory and access the files therein. Without execute access to a directory, a user is not allowed to access the files in that directory independent of the permissions on the files themselves.